Understanding the intricacies of federal regulations can be challenging, especially when it comes to healthcare privacy. This comprehensive guide to Health Insurance Portability and Accountability Act (HIPAA) violations is designed to illuminate the most common missteps and breaches that can compromise patient information, leading to legal consequences and undermining trust in healthcare providers.
What is a HIPAA Violation?
A HIPAA violation refers to a failure to comply with the provisions of the Health Insurance Portability and Accountability Act, a crucial set of regulations enacted in 1996 to safeguard medical information and ensure patient privacy. Violations occur when there is an unauthorized use or disclosure of Protected Health Information (PHI) that does not adhere to the standards set by HIPAA.
These infractions may vary in severity, ranging from improper handling of patient data within an organization to large-scale breaches involving unauthorized access by external parties. While some violations might be accidental, others involve deliberate breaches of privacy and can lead to significant penalties for the entities involved.
What is HIPAA and Who Does It Apply To?
HIPAA, or the Health Insurance Portability and Accountability Act, is a landmark piece of legislation enacted in 1996 in the United States. Its primary objective is to safeguard the privacy and security of individuals' health information. HIPAA establishes national standards for the electronic exchange of health information and sets guidelines to protect the confidentiality and integrity of patients' data.
Who Does HIPAA Apply To?
Healthcare Providers: HIPAA applies to a broad range of healthcare providers, including doctors, nurses, hospitals, clinics, and pharmacies. Essentially, any entity that furnishes medical services and handles patient information falls under the purview of HIPAA.
Health Plans: Insurance companies, health maintenance organizations (HMOs), and government programs like Medicare and Medicaid are considered health plans. HIPAA ensures that these entities adhere to strict standards when it comes to handling individuals' health information.
Healthcare Clearinghouses: Entities that process non-standard health information into standard formats fall under the category of healthcare clearinghouses. These organizations play a role in facilitating the smooth exchange of health information.
Business Associates: HIPAA extends its reach beyond traditional healthcare entities to include business associates. These are individuals or organizations that perform functions or services on behalf of a covered entity that involve the use or disclosure of protected health information (PHI). Business associates can include IT service providers, billing companies, and consultants.

What is a PHI Violation?
A PHI (Protected Health Information) violation occurs when there is unauthorized access, use, or disclosure of an individual's sensitive health information that is protected under HIPAA. This breach of privacy can take various forms, such as unauthorized access by healthcare professionals, improper sharing of patient records, or security lapses leading to the exposure of electronic health information. PHI violations are serious breaches of confidentiality and are subject to legal consequences and penalties under HIPAA regulations. Ensuring the security and privacy of PHI maintains the trust and integrity of healthcare systems.
15 Examples of HIPAA Violations
Unauthorized Access
Unauthorized access to Protected Health Information (PHI) is a serious violation of the Health Insurance Portability and Accountability Act (HIPAA). This occurs when individuals, without proper authorization, access sensitive health information. Here are a few examples:
- A healthcare employee accessing a neighbor's medical records out of curiosity.
- Unauthorized personnel viewing the medical history of a colleague without a valid reason.
- Inappropriate access to PHI by an ex-employee who still has access credentials.
To mitigate unauthorized access risks, enforce strict access controls based on job roles and conduct regular HIPAA training. Implement audit trails to monitor access, promptly terminate unnecessary credentials, and have an incident reporting and response plan. The adoption of advanced security measures, including encryption and multi-factor authentication, enhances overall data protection. These measures collectively foster a secure environment that prioritizes patient privacy and ensures compliance with HIPAA regulations.
Insufficient Data Encryption
Insufficient data protection under HIPAA regulations refers to the failure of a covered entity or business associate to adequately safeguard Protected Health Information (PHI), both electronically stored (ePHI) and in physical form. This can manifest in various ways, including but not limited to inadequate access controls, lack of data encryption, poor data storage procedures, and not having proper data disposal methods in place.
For example, if a healthcare provider does not have proper firewalls or encryption for their electronic records system, it can lead to unauthorized access and potential data breaches. Similarly, if physical records containing PHI are not stored securely and are accessible to unauthorized personnel, this too constitutes insufficient data protection.
To avoid such HIPAA violations, organizations must implement comprehensive security measures. These could include:
- Conducting regular risk assessments to identify and address vulnerabilities.
- Ensuring that all electronic communication containing PHI is encrypted.
- Adopting secure data storage practices with robust access controls.
- Providing thorough training for staff on PHI protection protocols.
- Developing and enforcing policies regarding the handling and disposal of paper records containing PHI.
One real-life example of a breach due to insufficient data protection is the case of the University of Rochester Medical Center, which faced HIPAA penalties after losing an unencrypted flash drive containing patient information. The organization paid a settlement of $3 million to the Office for Civil Rights (OCR) for the incident, which represents the serious implications of not adhering to sufficient data protection standards.
Lost or Stolen Devices
HIPAA violation involving lost or stolen devices occurs when an electronic gadget that houses Protected Health Information (PHI) goes missing or is unlawfully taken. This type of breach not only undermines patient confidentiality but also potentially exposes vulnerable data to unauthorized individuals, possibly leading to medical fraud or identity theft. Common pieces of technology that fall into this category include but are not limited to, mobile devices, laptops, and USB drives.
For example, a notable case was in 2017 when Lifespan announced that a work laptop was stolen from an employee's car. Because the laptop was neither password-protected nor encrypted, the incident resulted in the exposure of personal data for over 20,000 patients.
To prevent such violations, the following measures can be implemented:
- Conducting regular employee training on proper device handling and storage policies to ensure that all staff members understand the significance of safeguarding PHI.
- Establishing stringent physical security measures, such as using secure lockers and implementing sign-out policies for devices taken offsite.
- Encrypting all devices to protect data, Lost or stolen devices represents a significant HIPAA violation that involves the misplacement or illicit acquisition of electronic equipment holding Protected Health Information (PHI). This category of breach jeopardizes patient privacy and can lead to sensitive data being accessed by unauthorized personnel — a situation ripe for medical fraud or identity theft. Commonly implicated devices include mobile phones, laptops, and USB drives, all of which may contain confidential patient information.
Improper Disposal of PHI
Improper Disposal of PHI refers to the failure to adequately destroy or manage the disposal of Protected Health Information (PHI) when it is no longer needed. PHI encompasses a broad range of information, including patient health records, billing information, and any data that could be used to identify a patient. HIPAA regulations require that all forms of PHI, whether in paper or electronic format, must be disposed of securely to protect against unauthorized access or breaches.
Examples of Improper Disposal of PHI include:
- Tossing patient records into a public dumpster without shredding them first.
- Selling or discarding used computers or other electronic devices without properly erasing the stored PHI.
- Accidentally leaving printed PHI in common areas where unauthorized individuals could access it.
- Failing to have secure recycling bins for PHI could lead to documents being recovered by third parties.
To avoid the mishandling and improper disposal of PHI, healthcare organizations must establish and enforce strong policies and procedures. These include:
- Training staff thoroughly on the significance of PHI privacy and the proper methods for disposal.
- Implementing a 'clean desk policy' to ensure that sensitive information is not left out in the open.
- Regularly scheduling secure shredding services for paper documents that contain PHI.
- Utilizing To avoid the mishandling and improper disposal of PHI, healthcare organizations must establish and enforce strong policies and procedures. These include:
- Training staff thoroughly on the significance of PHI privacy and the proper methods for disposal.
- Implementing a 'clean desk policy' to ensure that sensitive information is not left out in the open.
- Regularly scheduling secure shredding services for paper documents that contain PHI.
- Utilizing certified software to wipe electronic devices, or physically destroying hard drives and other storage media that cannot be wiped.
- Ensuring bins for sensitive documents are securely locked and only accessible to authorized staff.
Real-life cases of improper disposal of PHI include the incident at the New England Dermatology and Laser Center, which resulted in a hefty fine of $300,640 in 2022. An example of lax disposal methods was also seen in the case of Affinity Health Plan, Inc., which in 2013 was fined over $1.2 million after returning leased photocopiers that contained PHI on their hard drives without erasing the data first.
Employee Snooping
Employee snooping is a HIPAA violation that occurs when healthcare personnel inappropriately access and view the medical records of patients without a legitimate need for such information. This breach compromises the privacy and confidentiality of patients' health data.
Examples:
- A nurse accesses the medical records of a celebrity admitted to the hospital out of curiosity, without any involvement in the patient's care.
- An employee views the records of a colleague, family member, or friend without a valid work-related reason for doing so.
Preventing employee snooping involves implementing strict access controls, conducting regular HIPAA training, and fostering a culture of respect for patient privacy within healthcare organizations. Regular audits and monitoring of access logs can help detect and deter unauthorized access.
Real-Life Cases:
- In 2011, a case involved a nurse and 3 employees at a medical facility in Tucson who accessed the medical records of a famous person. The employees and the nurse faced employment termination.
- Another incident in 2022 involved an employee at a healthcare facility in Alberta who inappropriately accessed patient records, leading to a $6000 fine. These cases underscore the importance of robust measures to prevent unauthorized access by healthcare personnel.
These real-life examples emphasize the significance of addressing employee snooping through stringent security measures, training, and consequences for violations to safeguard patient privacy.
Disclosure without Consent
Disclosure without consent is a HIPAA violation that occurs when Protected Health Information (PHI) is shared with unauthorized individuals or entities without the patient's explicit consent. This violation compromises the privacy and confidentiality of sensitive health information.
Examples:
- A healthcare provider shares a patient's medical history with a family member without the patient's consent.
- Unauthorized sharing of patient records with external parties, such as marketers or researchers, without obtaining proper consent.
To prevent this violation, individuals should be vigilant about granting explicit consent for the sharing of their health information. Healthcare providers should implement robust consent management systems and ensure that employees are well-trained on the importance of obtaining patient consent before disclosing any PHI.
For example, in 2019, a medical center in New York faced a lawsuit when a nurse disclosed a patient's HIV status to the patient's employer without consent. The breach led to legal consequences and highlighted the critical need for maintaining patient confidentiality.
These real-life cases underscore the importance of stringent privacy measures to prevent unauthorized disclosure and the potential legal ramifications for healthcare entities and individuals involved.
Failure to Conduct Risk Assessments
The HIPAA violation of failure to conduct risk assessments occurs when healthcare organizations neglect to perform comprehensive evaluations of potential risks to the confidentiality, integrity, and availability of Protected Health Information (PHI). Risk assessments are a fundamental component of HIPAA compliance, and the failure to conduct them puts patient data at risk.
Examples:
- A healthcare entity fails to regularly assess the security measures of its electronic health record system, leaving vulnerabilities unaddressed.
- A clinic neglects to evaluate the risks associated with the physical security of paper records, potentially exposing patient information to unauthorized access.
To avoid this violation, establish a systematic approach to conducting regular risk assessments. This includes identifying potential risks, evaluating the effectiveness of security measures, and implementing necessary updates. Staff training on risk assessment procedures is important as well.
For example, in 2018, a healthcare provider in Colorado faced penalties for failing to conduct adequate risk assessments, resulting in a data breach. The incident highlighted the importance of regularly assessing and addressing security risks to prevent breaches.
These real-life examples emphasize the critical role of regular risk assessments in maintaining the security and confidentiality of patient information, as well as the legal ramifications for organizations that fail to fulfill this obligation.
Inadequate Training
Inadequate training stands as a fundamental flaw leading to HIPAA violations. Employees must have a thorough understanding of HIPAA compliance requirements to safeguard Protected Health Information (PHI) adequately. Without proper training, employees may not grasp the significance of HIPAA regulations or comprehend the correct protocols for handling PHI.
Examples of issues resulting from inadequate training include:
- Employees might inadvertently leave devices containing PHI in unsecured locations.
- Staff could unknowingly share PHI with unauthorized personnel.
- Improper disposal of PHI documents due to ignorance of the correct procedures.
- Personnel might access PHI from unsecured networks or locations, increasing the risk of data breaches.
To mitigate these risks, HIPAA mandates training for all workforce members who handle PHI. This training is required upon hiring a new employee when there are updates in the regulations, and periodically to refresh and update the employees' knowledge. Comprehensive training courses, like those offered by Inspired eLearning and similar organizations, provide online HIPAA compliance training, which can be an efficient way to ensure employees have the knowledge necessary to avoid violations.
The absence of adequate training not only elevates the likelihood of HIPAA violations but also exposes healthcare organizations to legal risks and significant financial penalties. Therefore, emphasis on consistent and recurring training is not merely a recommendation but a regulatory requirement for compliance under HIPAA.
Delayed Breach Notification
Delayed breach notification is a significant violation under the HIPAA Breach Notification Rule, which stipulates immediate action following a data breach involving Protected Health Information (PHI). Entities are required to notify affected individuals and the Department of Health and Human Services (HHS) Office for Civil Rights (OCR) "without unreasonable delay" and within 60 days of discovering the breach.
Consequences of delayed notifications include:
- Potential for affected individuals to remain unaware and thus unable to take protective measures against identity theft or fraud stemming from the breach.
- Further erosion of trust between patients and healthcare providers due to perceived negligence.
- Increased scrutiny from regulators upon discovering a delay in breach disclosure.
For larger breaches impacting more than 500 individuals, covered entities must also notify prominent media outlets within the affected geographic area, ensuring public awareness of the breach's impact on their private data. Furthermore, if a breach affects fewer than 500 individuals, the entity must maintain a log of such breaches and report to the OCR annually.
The consequences of delayed notifications have led to substantial settlements being reached with entities that failed to comply. For example:
- The Oklahoma State University Center for Health Sciences agreed to an $875,000 settlement for delayed breach notifications alongside resolving additional HIPAA violations.
- Presence Health incurred a $475,000 penalty for a month's delay in issuing breach notifications.
- CoPilot Provider Support Services Inc. faced a $130,000 settlement with the NY Attorney General for similar delayed notification issues.
Therefore, to prevent these violations and their associated penalties, establish well-defined internal reporting policies, ensure thorough and timely breach details disclosure to the OCR and media, as applicable, and post-breach notifications on their website if required.
This commitment to timely response not only aligns with legal obligations but also reinforces the provider's dedication to patient privacy and their overall trustworthiness in handling sensitive health information.
Lack of Business Associate Agreements
A lack of Business Associate Agreements (BAAs) represents one of the more prevalent HIPAA violations, reflecting a gap in enforcing compliance across the spectrum of a covered entity's partnerships. BAAs are legal contracts that specify each party's responsibilities concerning Protected Health Information (PHI), serving as a critical compliance tool for third-party vendors who have access to or manage PHI on behalf of a healthcare organization.
Violations related to BAAs may include:
- Not having a signed BAA in place before sharing PHI with vendors or subcontractors.
- Failure to update existing BAAs to comply with the changes introduced by the HIPAA Omnibus Rule.
- Working with business associates who do not follow the HIPAA Security Rule and Privacy Rule standards.
Recent settlements highlighting the importance of adhering to the BAA requirement include:
- North Memorial Health Care of Minnesota reached a $1.55 million settlement for failing to enter into a BAA with a major contractor.
- Raleigh Orthopedic Clinic, P.A. of North Carolina was fined $750,000 for not securing a HIPAA-compliant BAA with a potential business associate.
- Care New England Health System settled for $400,000 due to the failure to update business associate agreements.
- MedEvolve Inc. paid a $350,000 settlement for lacking a business associate agreement with a subcontractor amongst other HIPAA violations.
Covered entities must undertake due diligence in executing BAAs with all business associates before PHI is provided to them. The agreements should clearly delineate the permissible uses and disclosures of PHI and ensure that business associates employ appropriate safeguards. Without these binding agreements, both the covered entity and the business associate open themselves to substantial risk and potential legal ramifications.
Instituting a comprehensive BAA process for vetting and managing agreements is imperative in maintaining HIPAA compliance and safeguarding patient privacy. This process should include regular audits to ensure all agreements remain up-to-date and reflect the current state of affairs in the rapidly evolving arena of health information security.
Ignoring Minimum Necessary Rule
The Minimum Necessary Rule is a key component of HIPAA, emphasizing that healthcare providers and associated entities must make reasonable efforts to limit the use or disclosure of, and requests for, Protected Health Information (PHI) to the minimum necessary to accomplish the intended purpose. This principle is foundational to maintaining patient privacy and ensuring the security of sensitive health data.
Neglecting the Minimum Necessary Rule can lead to breaches such as:
- Sharing more PHI than is required for a particular task or transaction.
- Improper exposure of comprehensive medical records when only specific information is needed.
- Excessive data access permissions are granted to employees who require limited information to complete their job functions.
For example, when a health insurance company requests patient information, it typically requires essential facts like the number of clinic visits rather than a complete medical history. Adhere to the “minimum necessary” principle, as oversharing can contribute to potential HIPAA violations.
For example, the University of California Los Angeles Health System was fined $865,500 for employees’ unauthorized access to medical records, indicating a deficiency in enforcing the minimum necessary standards.
Compliance with the Minimum Necessary Rule entails establishing policies and procedures that limit PHI disclosures, training workforce members to understand the necessary limits on PHI usage, and employing access controls to prevent unauthorized access to sensitive health information. These actions are not merely best practices but legal requirements meant to protect patient data from overexposure.
Healthcare organizations must regularly review policies related to the Minimum Necessary Rule to ensure they remain effective and respond to the evolving medical work environment. Taking preemptive measures and regularly reinforcing these principles among employees can substantially mitigate the risk of this type of HIPAA violation.
Security Rule Violations
Violations of the HIPAA Security Rule encompass a broad range of failures to implement and maintain the necessary safeguards to protect electronic Protected Health Information (ePHI). The Security Rule mandates three types of safeguards: administrative, physical, and technical. Each category contains a mix of required and addressable implementation specifications which are designed to be flexible and scalable to the needs of different organizations.
Examples of HIPAA Security Rule violations include:
- Failure to establish cybersecurity measures like firewalls and intrusion detection software.
- Not implementing access control measures to restrict unauthorized ePHI access.
- Absence of audit controls to regularly review access and activity logs concerning ePHI.
- Inadequate data integrity policies to ensure ePHI has not been altered or destroyed improperly.
- Lack of transmission security, leaving ePHI transmitted over networks vulnerable to interception.
Real-world cases of Security Rule violations resulting in significant penalties:
- Anthem Inc. suffered a breach impacting the ePHI of nearly 79 million people and agreed to a record $16 million settlement with the OCR for allegedly failing to implement adequate security measures.
- Premera Blue Cross paid $6.85 million to settle potential violations of the Security Rule related to a breach affecting over 10.4 million individuals.
Maintaining Security Rule compliance revolves around regular risk assessments, implementing corresponding security measures, and responding to new threats. Organizations must also periodically train their staff on the newest security practices and make updates to their security policies and procedures whenever necessary.
While compliance demands proactive and systematic approaches, the Security Rule's flexibility permits entities to tailor their security measures to their size, complexity, and capabilities, as well as to potential risks to ePHI.
Therefore, consistent vigilance and adaptation of security practices are vital to preventing Security Rule violations, protecting patient data, and avoiding the substantial fines and damage to reputation that comes with such breaches.
Privacy Rule Violations
Violations of the HIPAA Privacy Rule are serious infringements that involve the misuse or improper disclosure of Protected Health Information (PHI). The Privacy Rule establishes national standards for the protection of individuals' medical records and other personal health information and applies to health plans, healthcare clearinghouses, and healthcare providers that conduct certain healthcare transactions electronically.
Privacy Rule violations can include actions such as:
- Discussing patients' health information without their consent in a public setting.
- Not obtaining proper patient authorization for uses and disclosures of PHI is not otherwise allowed by the Privacy Rule.
- Releasing PHI to unauthorized parties, such as family members or friends, without a patient's explicit consent.
- Not providing patients with access to their medical records upon request.
- Using or disclosing more PHI than necessary (minimum necessary requirement).
Noteworthy instances of Privacy Rule violations include:
- New York-Presbyterian Hospital and Columbia University Medical Center had to pay $4.8 million in HIPAA settlements due to the unauthorized disclosure of ePHI of 6,800 individuals.
- CVS Pharmacy agreed to pay $2.25 million and implement a corrective action plan after disposing of PHI in a way that did not safeguard patient confidentiality.
In response to such violations, it's incumbent upon covered entities to ensure they have appropriate policies and procedures in place that align with the HIPAA Privacy Rule. This includes proper patient authorization forms, adequate training of staff to handle PHI responsibly, and establishing sanctions for non-compliance by workforce members.
To avoid such violations, conduct regular audits of your privacy practices and make sure that your employees understand the implications of the Privacy Rule. Also, inform patients about their rights under HIPAA and the ways in which their information is protected by their healthcare providers.
Failing to adhere to the Privacy Rule not only risks the privacy of sensitive health information but can result in legal actions, financial penalties, and a loss of trust from patients and the public. Compliance efforts, therefore, serve as both a legal requirement and a cornerstone of ethical healthcare practice.
Failure to Provide Access
Under the HIPAA Privacy Rule, individuals have the right to obtain a copy of their health records, also known as the right to access. Denial of access to patient records is considered a major violation. Healthcare organizations are required to furnish this information promptly, generally within 30 days of the request, with a single 30-day extension permitted if necessary.
Issues that fall under failure to provide access include:
- Not responding to a patient's request for access to their PHI.
- Charging fees for access that are not cost-based and therefore exceed what is allowed under HIPAA.
- Providing access in a manner or format that is not reasonable or convenient for the patient.
- Failing to inform patients of their right to access their PHI.
Some historical penalties for denying access include:
- Cignet Health of Prince George’s County paid a civil money penalty of $4.3 million to the Office for Civil Rights (OCR) for violations that included denying patients access to their medical records.
- Pagosa Springs Medical Center reached a $111,400 settlement due to the lack of timely action in terminating a former employee's access to ePHI and other HIPAA noncompliance issues.
Healthcare providers must establish clear procedures for responding to access requests, which include training staff on the legal requirements and developing systems that make the retrieval and delivery of patient data as efficient as possible. Additionally, organizations are advised to document all access requests and their outcomes to demonstrate compliance if their practices ever be questioned by regulators.
The consequences of failing to provide access can be substantial, not just in terms of penalties but also in the deterioration of patient trust and potential harm to individuals who may need their health information for their care or other purposes. Proactively managing patient access rights is not only good practice but also a legal obligation in accordance with HIPAA mandates.
Inadequate Patient Authentication
Inadequate patient authentication is a significant issue under HIPAA, where healthcare providers fail to properly verify the identity of an individual before providing access to their Protected Health Information (PHI). HIPAA requires covered entities to implement reasonable and appropriate verification procedures to ensure that PHI is not improperly disclosed.
Implications of inadequate patient authentication include:
- Unauthorized access to PHI by individuals pretending to be someone they are not, potentially leading to identity theft or other fraud.
- Inadvertent disclosure of sensitive patient information to the wrong person, which is a direct infringement of patient privacy.
- The risk of medical identity theft, where an impostor may receive medical treatment, potentially altering the victim’s own medical records.
HIPAA does not prescribe specific authentication methods, allowing for flexibility. However, it does suggest a few verification measures, like:
- Requesting photo IDs.
- Using unique personal identifiers.
- Implementing biometric identifiers such as fingerprints, age verification or retina scans.
For example, the lack of adequate patient authentication has led to instances like the case involving the University of Texas MD Anderson Cancer Center, which resulted in a $4.3 million penalty due to the disclosure of ePHI to an unauthorized individual.
Apply multi-factor authentication (MFA) where feasible, which may include something the user knows (a password), something the user has (a security token), and something the user is (biometric verification). This approach provides an additional security layer to defend against unauthorized access.
Important HIPAA Violation Information
When grappling with the intricacies of HIPAA, be aware of the details that govern how violations are perceived, handled, and penalized. Understanding these aspects can help health organizations not only avoid costly mistakes but also foster a culture of compliance and respect for patient privacy.
Key pieces of HIPAA violation information include:
- Any potential violation involves the unauthorized use or disclosure of Protected Health Information (PHI).
- HIPAA sets detailed requirements for handling, storing, and transmitting PHI.
- The Office for Civil Rights (OCR) within the U.S. Department of Health and Human Services is responsible for enforcing the HIPAA standards.
- Violations can be reported by patients, and employees, or observed by compliance review conducted by the OCR.
Comprehending the subtleties of possible violations is necessary for establishing preventative measures and responding effectively if a breach does occur. The ramifications of non-compliance are extensive, ranging from financial penalties to criminal charges, depending on the nature and severity of the breach.

Every healthcare provider, business associate, and subcontractors who handle PHI should be conversant with HIPAA requirements to avert violations. Education, training, and ongoing review and reinforcement of policies and procedures can significantly mitigate the risk of HIPAA breaches. It’s not just about avoiding penalties but ensuring that the rights and privacy of patients are always preserved.
HIPAA Violation Misunderstandings
The complexities of HIPAA often give rise to misunderstandings and misconceptions, which can inadvertently lead to compliance issues. Clarifying these points can prevent unintentional violations and help entities maintain the privacy and security of Protected Health Information (PHI).

Common misunderstandings about HIPAA violations include:
- Private Conversations Myth: Belief that casual conversations between healthcare providers about a patient's care are always a violation. These are permissible if conducted privately and with discretion.
- Complete Privacy Misconception: The misbelief that HIPAA guarantees complete privacy under all circumstances. There are specific exceptions, such as when information is required by law or for public health activities.
- Minimum Necessary Overstatement: Some entities interpret the minimum necessary standard too strictly, hindering the appropriate exchange of information for patient care.
- Small Practice Exemption: Smaller healthcare practices sometimes wrongly assume that HIPAA does not apply to them. All covered entities, irrespective of size, must comply with HIPAA regulations.
- Encryption Confusion: There is a misconception that HIPAA demands encryption in all instances. While it strongly endorses encryption, it also allows for an equivalent level of protection if encryption is impractical.
- De-identified Information Overlook: It's commonly misunderstood that de-identified information is still bound by HIPAA. If all identifiers have been properly removed, HIPAA does not restrict the use or disclosure of such information.
Dispelling these myths and misunderstandings helps maintain compliance and protect patient information. It is important for covered entities and their business associates to stay informed about the accurate requirements and nuances of HIPAA to cultivate a culture that prioritizes adherence and the proper handling of PHI.
How are HIPAA Violations Uncovered?
HIPAA violations are uncovered through various means, and it's pivotal for healthcare entities to understand these mechanisms as part of their compliance strategies. Recognizing the ways in which breaches can be detected helps organizations prepare and prevent compliance oversights.
The main avenues through which HIPAA violations are discovered include:
- Investigations into Data Breaches: When a breach of Protected Health Information (PHI) occurs, the Office for Civil Rights (OCR) or state attorneys general may conduct thorough investigations to determine whether a violation of HIPAA rules was at the root of the incident.
- Complaints from Individuals or Employees: Complaints about covered entities or business associates can trigger an investigation. These can be filed by patients, employees, or other stakeholders who believe that a HIPAA violation has taken place.
- HIPAA Compliance Audits: Under its audit program, the OCR systematically reviews the policies and procedures adopted by covered entities and their business associates to ascertain whether they conform to the HIPAA Privacy, Security, and Breach Notification Rules.
- Spontaneous Screenings and Audits: While not always the result of a known incident, routine reviews and audits can uncover violations that may have otherwise gone unnoticed.
Even if a breach or complaint does not initially seem to indicate a HIPAA violation, subsequent investigations can reveal unrelated HIPAA violations that could still lead to financial penalties.
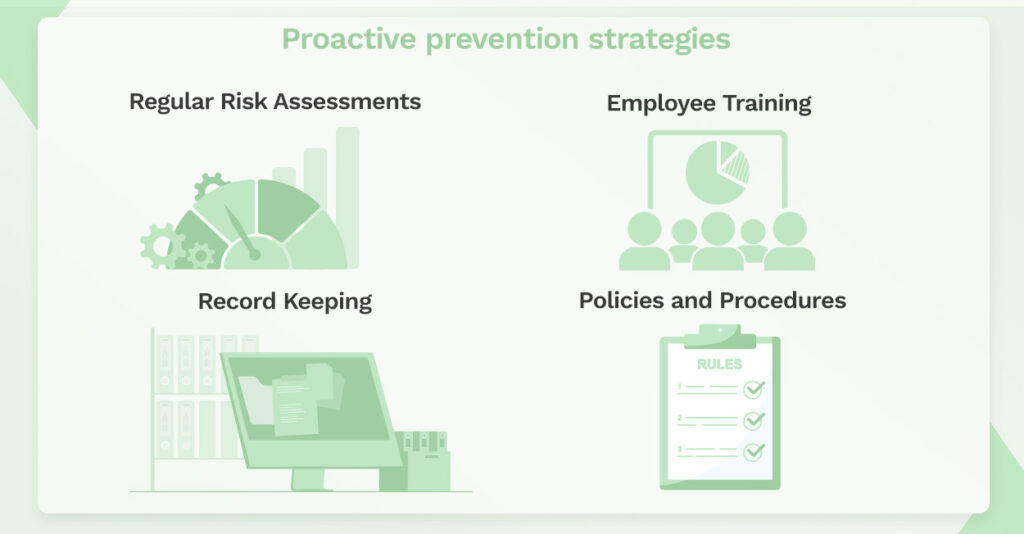
Proactive prevention strategies include:
- Regular Risk Assessments: Periodic evaluations to identify and address potential vulnerabilities to PHI.
- Employee Training: Continuous education for employees to ensure they are aware of HIPAA policies, recognize potential risks, and understand the importance of maintaining PHI security and privacy.
- Policies and Procedures: Establishing updated and clear policies that comply with HIPAA and reflect current security threats and technological changes.
- Record Keeping: Maintaining detailed records of compliance efforts, access controls, and incident response measures.
Understanding these potential discovery methods and maintaining vigilance in compliance measures is a key defense strategy against HIPAA violations and their consequences. Regular reviews to ensure adherence to the HIPAA Privacy, Security, and Breach Notification Rules are vital to safeguard patient information and uphold the integrity of healthcare organizations.
Recognized Security Practices
The term "recognized security practices" refers to processes and methods that are acknowledged within the healthcare and cybersecurity industries for effectively safeguarding electronic Protected Health Information (ePHI). These practices are developed on the basis of established standards, guidelines, and practices, and they serve to enhance an entity's posture in complying with the HIPAA Security Rule.
Importance of utilizing recognized security practices:
- Compliance Maintenance: Implementing such practices helps in maintaining compliance with HIPAA regulations and can potentially mitigate penalties in the event of a HIPAA audit or investigation following a data breach.
- Risk Management: Adopting recognized practices aids in the risk management process, identifying vulnerabilities, implementing necessary safeguards, and proactively preventing potential data breaches.
- Industry Trust: Showcasing a commitment to the highest standards of data security and patient privacy builds trust among patients and peers.
Examples of recognized security practices include:
- Following the guidelines laid out by the National Institute of Standards and Technology (NIST), such as the NIST Cybersecurity Framework.
- Implementing the controls and benchmarks disseminated by the Center for Internet Security (CIS).
- Complying with international standards like ISO/IEC 27001 for information security management.
Organizations are encouraged to keep abreast of these practices, regularly review their security measures, and adapt to the evolving landscape of threats. This ongoing adjustment helps protect sensitive health information from unauthorized access or disclosure.
Integration of recognized security practices into the organization’s security policies can position the covered entity to argue for lessened culpability and potentially lower fines if a violation occurs. It also demonstrates due diligence in the protection of ePHI under the scrutiny of federal enforcement agencies.
What are the Penalties for Violations of HIPAA Rules?
The penalties for violations of HIPAA rules can be severe and vary according to the nature of the infraction and the level of negligence involved. Penalties can be civil or criminal, with consequences ranging from monetary fines to imprisonment.
HIPAA violation examples and settlements include significant financial consequences, as seen in cases like the $16 million settlement with Anthem for the massive 2015 breach, and Advocate Health Care's $5.55 million settlement for multiple potential violations.
Be aware that the penalties for HIPAA violations underscore the critical importance of compliance. Establishing robust privacy and security practices and maintaining HIPAA compliance can prevent infractions and avoid the resulting penalties. It's not merely a financial imperative but a legal and ethical one as well.
HIPAA Violation Fines and Penalties
HIPAA violation fines and penalties serve as a stringent reminder of the importance of compliance and the potential consequences of negligence. These penalties are instituted by the Department of Justice and enforced by the Office for Civil Rights (OCR) within the Department of Health and Human Services (HHS).
A breakdown of the fines and penalties includes:
- Civil Penalties: Tiers of civil penalties range from fines as low as $100 per violation for issues that could not reasonably have been avoided, up to $50,000 per violation when willful neglect is involved but corrected within a required time period.
- Criminal Penalties: Criminal charges, which can include both fines and imprisonment, vary from $50,000 and up to one year in prison for simple violations, to fines of up to $250,000 and up to ten years in prison for offenses committed under false pretenses or with intent to sell or use PHI for harmful purposes or personal gain.
- Annual Maximums: There is an established annual maximum for each tier of civil penalties, with the highest being $1.5 million per year for uncorrected violations due to willful neglect.
Recent enforcement examples:
- A notable example includes the $16 million settlement with Anthem Inc. for potential HIPAA Rules violations stemming from a data breach that exposed the ePHI of close to 79 million individuals.
- The OCR's enforcement activities have also reached entities like the Texas Health and Human Services Commission, which was fined $1.6 million for violations including failure to remove ePHI access after an employee's departure.
Additionally, fines are categorically allocated:
- Reasonable Cause: Fines range from $100 to $50,000 per violation.
- Willful Neglect: Penalties range from a minimum of $10,000 to $50,000 per violation, with the potential for criminal charges.
Also, fines that are collected from HIPAA violation cases are now being directed to support further enforcement of HIPAA Rules. This includes providing restitution to victims of HIPAA breaches, signifying a more victim-centric use of the collected penalties.
Covered entities and their business associates should engage in robust training, enact risk assessments, and maintain comprehensive and up-to-date policies and procedures to avoid such penalties. Understand that HIPAA violation fines and penalties are not just punitive but are also meant to be corrective, incentivizing entities to improve their PHI protection efforts to prevent future violations.
The fines and penalties for HIPAA violations can be formidable, serving as a strong incentive for healthcare organizations and their partners to adhere strictly to HIPAA regulations. Strengthening HIPAA training, compliance efforts, and patient data protection practices not only minimizes the risk of a costly violation but also enhances the overall trust and integrity within the healthcare system.
Conclusion
HIPAA violations are a critical concern for anyone in the healthcare ecosystem handling Protected Health Information (PHI). They can have grave consequences, ranging from financial penalties to criminal charges, not to mention the potential harm to patients and erosion of public trust in healthcare institutions. As healthcare continues to integrate technology, the importance of HIPAA compliance grows even stronger. Entities must recognize that compliance is not a one-time initiative but an ongoing process that demands continual education, risk assessment, and the implementation of industry-recognized security practices.
With the internalization of the lessons from past violations and staying up-to-date with the evolving regulations, healthcare organizations can better protect patient information and uphold their legal and ethical obligations. The information provided herein should be a cornerstone for healthcare entities to evaluate and refine their compliance efforts proactively, ensure the protection of patient rights, and contribute to a more secure and trustworthy healthcare industry.
Start building with a free account
Frequently Asked Questions about HIPAA Violations
To avoid HIPAA violations, implement strict access controls, conduct regular staff training on privacy policies, encrypt sensitive data, and perform routine risk assessments. Employees should follow guidelines, obtain patient consent, and be cautious about sharing Protected Health Information (PHI).
Signs of HIPAA violations include unauthorized access to patient records, inadequate security measures, and breaches of patient confidentiality. Regular audits, monitoring access logs, and staying informed about HIPAA regulations help identify potential violations.
Anyone handling Protected Health Information (PHI), including healthcare professionals, administrative staff, and support personnel, can violate HIPAA. Non-medical individuals with access to patient data are also accountable for maintaining confidentiality and adhering to HIPAA regulations.
A HIPAA violation occurs when there is unauthorized access, use, or disclosure of Protected Health Information (PHI). This includes breaches of patient confidentiality, inadequate data safeguards, and failure to adhere to HIPAA privacy and security standards.
Yes, anyone handling Protected Health Information (PHI), regardless of their medical background, can violate HIPAA. This includes administrative staff, support personnel, and individuals in non-clinical roles who have access to patient information.
HIPAA violation fines vary based on the severity of the breach. Civil penalties range from $100 to $50,000 per violation, with an annual maximum of $1.5 million. Criminal penalties can lead to fines up to $250,000 and imprisonment for up to 10 years for intentional violations. The fines emphasize the importance of safeguarding patient privacy and complying with HIPAA regulations.