Last year, the number of data breaches almost doubled, jumping from 1,802 to 3,205, as reported by Statista. This shows how important it is to have strong online database management in our digital world. With more cyber threats, databases have become assets that need strong protection. Managing your online databases securely means more than just storing data. It also means controlling who can access it to keep sensitive info safe.
In this post, we'll share tips for protecting your data from hackers and cyber threats. These practices are the first step in understanding how to manage your databases safely.
What is Secure Online Database Management
Secure online database management protects your data from hackers and cyber threats. It uses many security tools and tech to protect your database systems. This includes keeping apps, data, and endpoints safe and ensuring your important information stays secure.
Secure database management prevents data misuse, damage, and unauthorized access. Good security plans protect your data and the systems that manage it. It is also important to keep physical and virtual servers safe and ensure your data is always secure.
Focusing on strong database security allows companies to keep their data reliable and accessible. This builds trust with customers and partners. Secure online database management helps you deal with info security issues, keeping your valuable data safe.
Why is Secure Online Database Management Important
Companies use databases to store important information, making them a big target for hackers. If a database gets hacked, it can cause big financial losses and harm a company's reputation.
If security is poor, data can get damaged or accessed without permission. As hackers get smarter, companies must keep up with the latest security methods. They need strong plans to protect their data.
Protecting data is a constant effort in our digital age. Without strong security, a company can face many threats. Focusing on secure database management helps businesses stay reliable and meet legal standards, helping it succeed even when facing challenges.
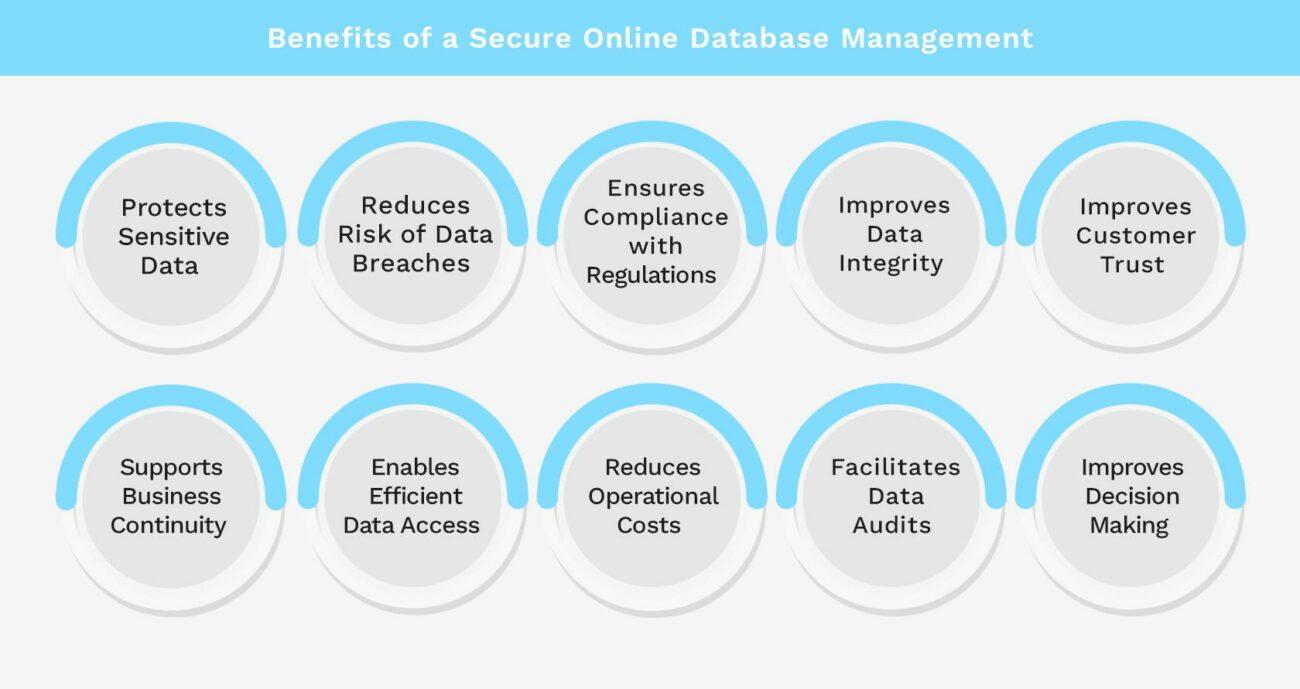
Benefits of a Secure Online Database Management
Using secure online database management has many benefits. Here are the most important ones:
Protects Sensitive Data
Secure online database management ensures that sensitive information like customer details, financial records, and intellectual property is protected from unauthorized access. Encryption and strong access controls prevent hackers from stealing or tampering with data. This helps maintain the privacy and integrity of your information.
Reduces Risk of Data Breaches
Secure online database management implements strong security measures. Regular security updates, vulnerability assessments, and monitoring tools help identify and fix potential weak points, lowering the chances of a costly and damaging data breach.
Ensures Compliance with Regulations
Secure database management helps your business comply with data protection regulations like GDPR, HIPAA, or CCPA. Compliance reduces the risk of legal penalties and fines. It also builds customer trust, showing them that their data is handled responsibly.
Improves Data Integrity
Security measures like access controls and regular backups ensure that your data remains accurate and consistent. This prevents unauthorized changes and accidental data loss. Maintaining data integrity is key for making reliable business decisions and providing accurate reports.
Improves Customer Trust
Customers are more likely to trust your business if they know their data is secure. Secure online database management protects customer information from being exposed or misused. This trust can lead to stronger customer relationships and a better reputation in the market.
Supports Business Continuity
Secure database management includes regular backups and disaster recovery plans that help your business continue operating in case of a data loss event. These measures ensure that you can quickly restore data and minimize downtime. This is essential for maintaining operations and avoiding financial losses.
Enables Efficient Data Access
While security is a priority, secure online database management also ensures that authorized users can easily access the data they need. This balance between security and accessibility helps your team work efficiently. Controlled access prevents unauthorized users from interfering with the database.
Reduces Operational Costs
Investing in secure database management prevents costly data breaches and downtime. It reduces the need for emergency fixes and legal fees associated with data breaches.
Facilitates Data Audits
Secure online database management systems often include audit trails that track who accessed or modified the data and when. This feature helps in conducting audits, ensuring accountability, and detecting any suspicious activity. Regular audits are essential for maintaining the health of your database.
Improves Decision-Making
With secure online database management, you can trust that the data you use for decision-making is accurate and up-to-date. Reliable data leads to better decisions, which can improve business performance and outcomes. This benefit underscores the importance of a secure and well-maintained database system.
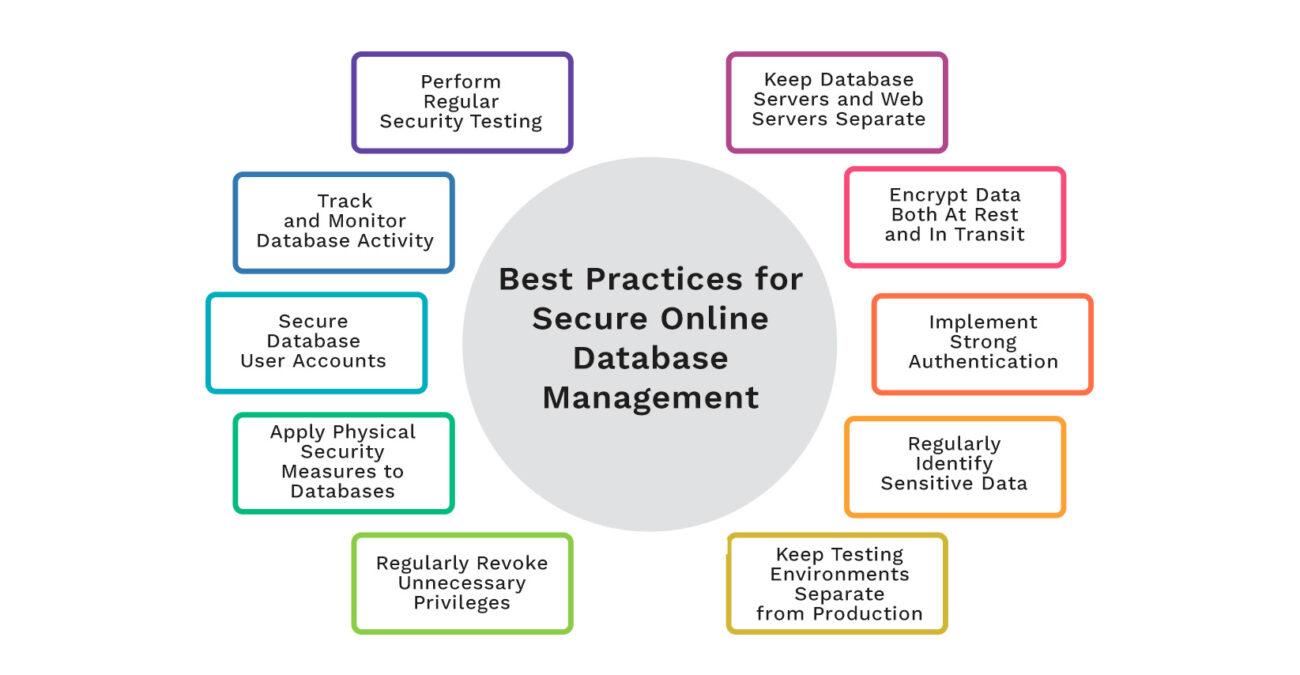
Best Practices for Secure Online Database Management
To keep your online database safe, it's important to follow best practices that protect your data from threats and ensure reliable access. Here are some key steps you should take.
Keep Database Servers and Web Servers Separate
Keeping database servers away from web servers increases security. This reduces the chance of unauthorized access. It keeps your data safe from threats. This method gives you big advantages in managing your database safely.
Encrypt Data Both At Rest and
In Transit
Encrypting data is a top way to protect it. It keeps information secret, whether it's stored or moving. This strong encryption helps keep your data safe and increases your database management.
Implement Strong Authentication
Strong authentication ensures that only the right people get into your databases, adding an extra layer of security. Using two-factor authentication or biometrics makes your data even safer.
Regularly Identify Sensitive Data
It's important to know what data in your systems is most sensitive. This lets you focus on protecting it better. This approach makes your database more secure and helps you use your resources wisely.
Keep Testing Environments Separate from Production
Separating testing from production environments helps avoid problems and risks. It lets you test new things safely. This way, you don't risk your secure data or expose it to threats.
Regularly Revoke Unnecessary Privileges
Reviewing and taking away access when it's not needed lowers the risk of unauthorized actions.
Apply Physical Security Measures to Databases
Adding physical security, such as access controls and cameras, keeps your database safe. These steps are important for protecting your data and keeping it secure.
Secure Database User Accounts
Good policies for securing database accounts stop unauthorized access. Using strong passwords and updating them often is key to keeping your databases safe.
Track and Monitor Database Activity
Watching what's happening in your databases helps spot strange patterns or threats. Monitoring tools give you insights, which help you act fast if there's a security issue.
Perform Regular Security Testing
Testing your security often finds weak spots that hackers could use. Regular checks help you update your security to stay strong against threats. This ongoing check-up is important for keeping your data safe.
Build Your Secure Online Database with Kohezion
Kohezion offers a top-notch solution for keeping your online databases safe. It has Kohezion features that make managing data easy and secure. Users get to choose options that keep their important info safe and private.
Kohezion database security is serious about following data protection laws. Its easy-to-use interface helps you manage data while meeting legal standards. This makes it easier to keep your info safe and reduces the chance of data breaches.
It also has great monitoring tools to keep an eye on your database actions. This helps control who gets in and keeping a record of all changes. It helps create a secure space that fits your business needs.
Using Kohezion for your database needs increases your data security and makes managing your databases easier. These features help you protect your information from threats before they happen.
Conclusion
Keeping your online databases safe is essential with the growing cyber threats. You should keep your database servers separate from your web servers and use strong encryption. Properly managing user accounts and performing regular security checks are also important steps.
Companies need to stay alert to new threats. This guide highlights the need for strong security measures. Using these strategies will make your online databases safer and help your business stay secure.
Focusing on secure database management is a wise choice for your company's future. The actions you take now will protect important data later. This provides peace of mind and helps keep your business safe from risks.
If you have questions or need support regarding database management, feel free to contact us at Kohezion. We're here to help you with your data management needs.
Start building with a free account
Frequently Asked Questions
Keeping database and web servers minimizes the risk of a single breach compromising both systems. If an attacker gains access to the web server, they won't automatically have access to the database server. This separation also allows for better performance and management of each server type.
Database encryption converts data into a secure format that only authorized users can read. Encryption at rest secures data stored on disk, while encryption in transit protects data as it moves between servers or users. Using both types of encryption ensures comprehensive protection for your data throughout its lifecycle.
Continuously discovering sensitive data helps ensure that you are aware of all sensitive information stored in your database. This allows you to apply appropriate security measures and comply with data protection regulations. Regularly identifying sensitive data also helps you manage and protect it more effectively.
Monitoring database activity helps detect suspicious or unauthorized actions in real-time. Tracking who is accessing your database and what actions they are performing enables you to quickly identify potential security threats. Regular monitoring also allows you to respond to issues promptly and maintain the security of your database system.