The increased use of no-code database builders has made creating and managing databases much easier. Now, you can build your databases, define relationships, and create data structures visually without any programming knowledge required.
However, this raises the question: how do you ensure the security of these databases? How do you make sure nobody gets their hands on private info without permission?
This article will cover the top tips for locking down your no-code database and keeping your information safe from shady businesses.
We'll buid your first application for you. At no extra cost.
Let us build your first business application for free. Go from an idea to an application in under 2 weeks.

Understanding No-Code Databases
Let's break down what no-code databases are and why they can be both the coolest thing and a potential headache.
What Are No-Code Databases?
No-code databases are platforms or tools that allow you to create and manage databases without programming. You can visually design your database, configure relationships between different data sets, and even automate specific tasks. But the best part is that you can do all this without writing a single line of code, saving a ton of money and time.
Examples in Action
Some of the most widely used website-building platforms or project management tools that allow you to create databases instantly include Airtable, Google Sheets, and even CRM systems. These are incredibly convenient because they allow non-specialists to organize data and optimize workflow processes.
Security Risks
No-code databases can pose serious security risks if not handled properly. Global malware attacks reached 5.5 billion in 2022, an increase of 100 million from the previous year. Since these databases are often designed for ease of use rather than robust protection, they may lack some built-in security mechanisms found in more traditional databases.
When building a database with just a few clicks, it's easy to overlook access control or encryption. Also, since these platforms are usually based on cloud services, you're entrusting a third party to store your data. Your information could be vulnerable to threats if they experience a breach or error.
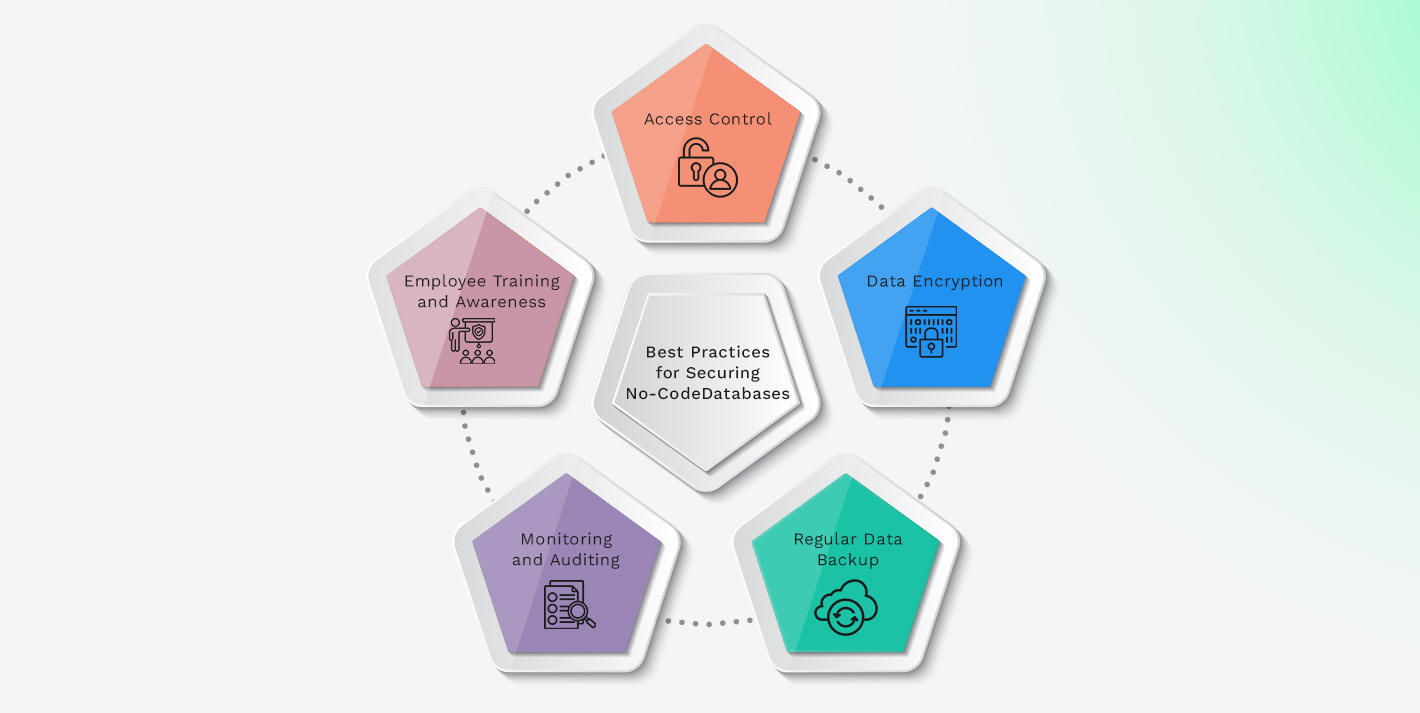
Best Practices for Securing No-Code Databases
So, how can we achieve high security for our no-code database? Let's determine which practices can help.
Access Control
In the access control section, we’ll discuss two primary approaches. The first one is the Role-Based Access Control (RBAC). In this approach, the database administrator can view and modify all data, whereas regular users can only view employee information without the ability to modify it. This uses specific tables to store roles and their corresponding access rights. When users authenticate, the system checks their role and applies the relevant data and function access rights.
User authentication and authorization are also crucial practices. Initially, the system verifies the user's identity and then grants or denies them specific actions within the database. The authentication process typically involves comparing the user-entered credentials with the data stored in the database. Passwords are usually stored in hashed format to increase security.
Implementing the cloud for telecom industries offers additional security and scalability, making these authentication and authorization processes more robust. Leveraging cloud solutions can help telecom companies manage vast amounts of data securely and efficiently. The cloud for telecom also enables seamless integration with existing infrastructure, allowing for more agile and responsive authentication systems.
Data Encryption
Encryption is one of the best ways to keep your data safe, both at rest and in transit. Encrypting data at rest means keeping data safe while it's just in the database. Encryption in transit means that your data stays secure while it's on the move over the network.
Encryption algorithms like AES (Advanced Encryption Standard) are commonly used to transform data into an unreadable format for encrypting data at rest. When encrypting data in transit, encryption protocols such as SSL/TLS are employed to establish a secure connection between the client and server.
Let's consider a scenario where a company stores confidential customer data, such as credit card numbers, in its database. Encrypting data at rest would safeguard this information from unauthorized access, even in case of a database breach. Using encrypted communication protocols like SSL/TLS during data transmission ensures that the data remains protected from interception by malicious actors.
Secure communication protocols protect data during transmission over the network. This includes employing protocols like HTTPS for websites and SSH for remote database access.
HTTPS combines the HTTP and SSL/TLS protocols to transmit data securely between the client and server. SSH facilitates secure remote connections to the server through authentication and encryption.
Regular Data Backup
Creating backups means you can always revert to the latest saved version if something goes wrong. This helps prevent data loss and facilitates quicker recovery from mishaps.
Backups can be stored in the cloud, external drives, or other devices. Specialized programs often automate this process, creating data copies and ensuring their integrity and availability.
If you own an online store, regular backups can quickly restore order and product data in case of a system failure or hacker attack. If data is accidentally deleted or corrupted, it can easily be recovered from the backup.
Determine how often to create backups and which methods to use for creation and storage. Depending on the volume of data and recovery requirements, backups can be made daily, weekly, or according to another schedule. Backup methods may include full, differential, or incremental copying.
Let's compare two examples:
- Financial Company: Making daily backups of financial transaction data helps keep financial information safe and ensures compliance with regulations.
- Educational Institution: Regular incremental backups of educational materials and learning outcomes ensure continuity of the educational process in case of system failure or data loss.
Monitoring and Auditing
Monitoring and auditing allow you to keep a close watch on your database in real time. Specialized tools and software analyze every transaction, query, and move made within the database as it happens.
This oversight is like having a data engineering company by your side, leveraging advanced analytics and cutting-edge technology to ensure the integrity and security of your digital assets.
Examples of use:
- Financial Sector. Real-time monitoring enables banks to detect suspicious transactions and prevent fraud quickly.
- Technology Company. A company can utilize real-time monitoring to monitor user activity and quickly address any access or data security concerns that arise.
For regular auditing of access logs and actions, specialized tools are typically used to analyze and record all user actions with the data.
Examples of use:
- Medical Clinic. Regular auditing of access logs helps the clinic monitor who has access to patient medical data and ensure their confidentiality.
- E-commerce Platform. Regular auditing of access and actions helps the platform detect and prevent unauthorized access to customer data and financial transactions.
Employee Training and Awareness
Employee training and awareness involves familiarizing staff with basic security rules when handling data. It also entails teaching them how to handle sensitive information properly.
Employees also need to learn technical tricks, such as creating secure passwords and recognizing phishing attacks. For example, employees in a financial firm can learn not to send sensitive customer data via email or store information on unencrypted USB drives.
Regular informational sessions, security newsletters, and checking employees' awareness levels are necessary to stay updated on all security news. For example, in an insurance company, employees are regularly briefed on the latest cyber threats and how to protect against them. These include cyber threats like malware, phishing attacks, DDoS attacks, etc. In 2023, phishing emerged as the most expensive method of initial attack, amounting to $4.9 million. Employees should also know how to use an SPF checker to ensure that emails are authenticated, reducing the risk of phishing attacks and data breaches.
To protect against phishing attacks, employees may be offered the following measures:
- Updating antivirus software and protection against malware;
- Training employees to recognize suspicious emails and websites;
- Using network firewalls and other DDoS attack protection measures;
- Regularly update security policies to keep them in line with the latest threats.
Create Your Secure No-Code Database with Kohezion
Creating a secure no-code database is straightforward with Kohezion. This platform allows users to design and manage custom databases without coding knowledge. Kohezion is user-friendly, making it accessible for professionals of all skill levels to manage data effectively.
With Kohezion, you can quickly set up your database to track, manage, and store data efficiently, all while enjoying the peace of mind that comes with robust security measures.
Conclusion
While databases are very useful, they can also be very vulnerable from a security point of view. But these problems have been around for a while, and there are enough solutions for them. Applying best practices can help you build sufficient protection for sensitive data. This way, you can enjoy the convenience of no-code solutions without constant worry about data leaks.
Start building with a free account
Author bio:

Frequently Asked Questions
Businesses should implement data encryption, access controls, and audit trails in their no-code databases to ensure compliance with data protection regulations such as GDPR, HIPAA, or CCPA.
They should also regularly review and update their privacy policies and procedures to meet regulatory requirements. Businesses may need to seek legal counsel or consult compliance experts to ensure they meet all relevant regulatory obligations.
User authentication ensures that only authorized individuals have access to sensitive data. Implementing strong authentication methods such as multi-factor authentication (MFA) or single sign-on (SSO) can help prevent unauthorized access and improve security.
In case of a data breach, businesses should immediately notify affected individuals and regulatory authorities as required by law. They should also investigate to determine the cause of the breach and take steps to remediate any vulnerabilities. This may include patching security flaws, improving access controls, and increasing data encryption measures to prevent future breaches.